Introduction to State Wide Area Networks (SWAN)
In today’s interconnected world, the need for efficient communication and data transfer is more critical than ever. Enter the state wide area network (SWAN), a powerful solution designed to link multiple sites over vast geographical distances. SWANs enable organizations—be they government agencies, educational institutions, or large corporations—to share resources seamlessly while maintaining robust security measures.
Imagine having an entire state’s worth of offices connected through a reliable digital backbone. With the right design and components in place, these networks facilitate smooth operations and enhance productivity across various sectors. But what exactly goes into crafting such an intricate system? Let’s dive deep into the essential elements that make up a state wide area network and explore how you can harness its full potential while ensuring top-notch security.
Components of a SWAN
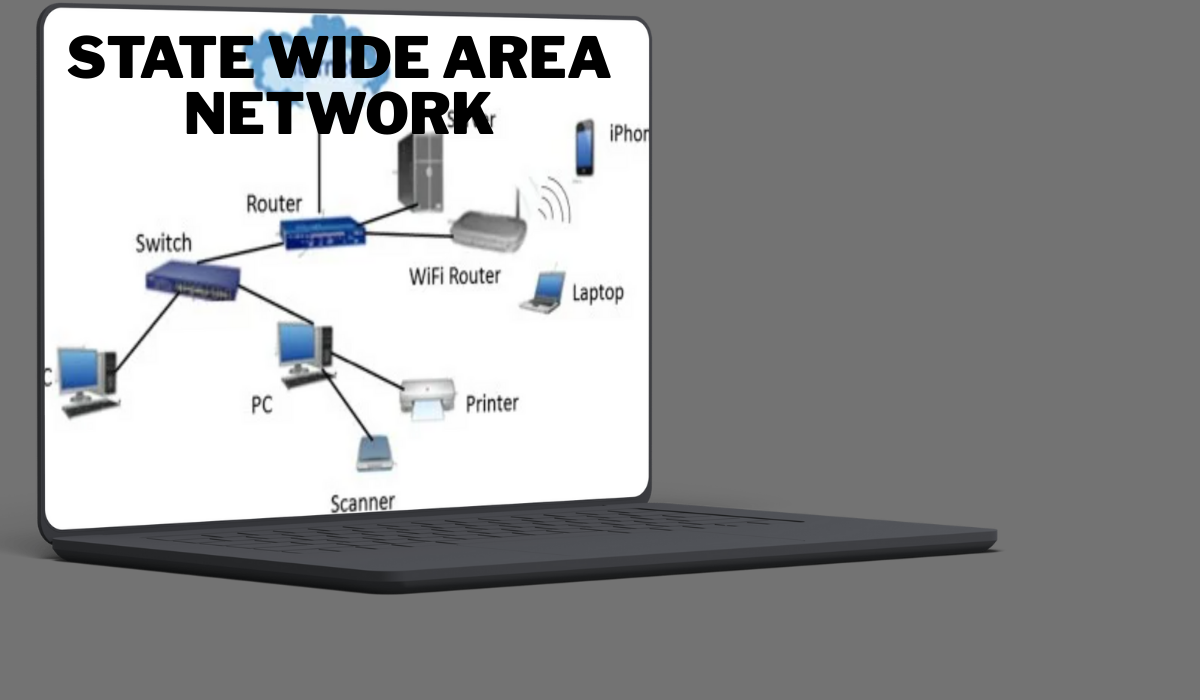
A State Wide Area Network (SWAN) comprises several key components that work together to ensure efficient communication across vast distances.
Routers are essential in directing data packets between different networks. They determine the best path for information, enhancing connectivity and performance.
Switches play a crucial role in managing local traffic within the network. By connecting devices like computers and printers, they facilitate seamless communication among users.
Firewalls serve as a protective barrier against unauthorized access. They monitor incoming and outgoing traffic, ensuring that only legitimate data flows through while blocking potential threats.
Servers provide centralized resources such as applications and file storage. This allows multiple users to access shared services effortlessly, fostering collaboration across various locations.
Each component is vital for creating a robust SWAN infrastructure, enhancing overall functionality and security throughout the network.
A. Routers
Routers are the backbone of any State Wide Area Network. They manage data traffic between different networks, ensuring seamless communication across vast distances.
These devices determine the best path for information to travel, directing packets efficiently. By connecting multiple local area networks (LANs), routers play a crucial role in linking various geographic regions.
Modern routers come equipped with advanced features like Quality of Service (QoS). This prioritizes critical applications, ensuring that essential services run smoothly even during peak usage times.
Additionally, many routers offer built-in security measures. Firewalls and intrusion detection systems help protect sensitive data from unauthorized access while traversing the network.
Choosing the right router is vital for optimal performance in a SWAN. The selection should align with specific needs such as bandwidth requirements and user capacity to ensure reliability and efficiency throughout the network.
B. Switches
Switches play a vital role in the architecture of a state wide area network. They serve as the backbone, connecting different devices within local networks and facilitating communication across vast distances.
These intelligent devices manage data packets by directing them to their respective destinations. Unlike simple hubs, switches can analyze incoming data and send it only to the intended recipient, enhancing efficiency.
In a SWAN environment, switches often handle large volumes of traffic. This capability ensures that data flows smoothly between various locations without bottlenecks or interruptions.
Choosing high-quality managed switches can provide additional benefits like VLAN support and traffic prioritization. These features allow for better control over network performance and security.
Investing in reliable switching technology is crucial for maintaining optimal functionality within a state wide area network ecosystem.
C. Firewalls
Firewalls play a crucial role in the architecture of a state wide area network. They act as gatekeepers, controlling incoming and outgoing traffic based on predetermined security rules. By doing so, they help protect sensitive data from unauthorized access.
Different types of firewalls exist to cater to various needs. Hardware firewalls provide robust protection at the network perimeter, while software firewalls offer flexibility on individual devices. Both are essential for maintaining a secure SWAN environment.
Employing advanced firewall features such as intrusion detection systems can enhance security further. These systems monitor traffic patterns and alert administrators about suspicious activities in real time.
Regular updates and configuration checks are vital for ensuring that your firewall remains effective against emerging threats. A well-maintained firewall serves not just as a barrier but also as an integral part of your overall cybersecurity strategy within a state wide area network setup.
D. Servers
Servers play a pivotal role in a state wide area network (SWAN). They serve as the backbone for data storage, processing, and management. With multiple locations connected over vast distances, servers ensure that information is accessible to authorized users across the network.
There are different types of servers within a SWAN. Application servers handle specific tasks like running software applications. Database servers manage large volumes of data securely and efficiently.
The performance of these servers directly impacts user experience. Slow or unresponsive server issues can lead to frustration among users relying on timely access to critical resources.
Moreover, proper configuration is essential for maximizing their capabilities. Load balancing distributes requests evenly across multiple servers, enhancing reliability and speed.
Securing these units against cyber threats adds another layer of complexity but is crucial in maintaining an efficient and safe SWAN environment. The right server setup paves the way for seamless communication between all nodes within the network.
Designing a Secure SWAN:
Designing a secure state wide area network requires careful planning and execution. A robust network topology is essential for ensuring efficient data flow while minimizing vulnerabilities. Opting for a hybrid or mesh topology can optimize redundancy, allowing for quick recovery in case of failures.
Data encryption plays a crucial role in safeguarding sensitive information as it travels across the network. Implementing strong encryption protocols protects data from unauthorized access and potential breaches.
Access control measures must be stringent to restrict who can enter the system. Role-based access controls help ensure that only authorized personnel have entry to critical areas of the SWAN.
Network monitoring is equally important; regular audits help identify unusual activity or weaknesses within the infrastructure. Real-time alerts allow swift action against any emerging threats, enhancing overall security posture significantly.
A. Network Topology
Network topology refers to the arrangement of different elements in a state wide area network. It plays a crucial role in determining how data flows and how devices communicate.
Common topologies include star, mesh, and hybrid configurations. Each offers unique advantages based on specific needs. For instance, a star topology is easy to manage but can create a single point of failure if the central hub goes down.
In contrast, mesh networks provide redundancy; every device connects to multiple others. This can enhance reliability but at the cost of increased complexity and installation time.
Strategic selection of topology affects performance and scalability. A well-planned design ensures optimal use of resources while maintaining security levels across the entire network landscape.
B. Data Encryption
Data encryption is a crucial aspect of securing a state wide area network. It transforms data into an unreadable format, ensuring that sensitive information remains protected from unauthorized access.
Implementing robust encryption protocols helps in safeguarding the integrity and confidentiality of transmitted data. Common methods include AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), each offering different levels of security based on organizational needs.
Moreover, end-to-end encryption ensures that only authorized users can decrypt the information at both ends of the communication channel. This approach significantly reduces vulnerabilities during data transfer across diverse locations within the SWAN.
An effective encryption strategy also includes regular updates to cryptographic keys. This practice helps mitigate risks associated with potential breaches or outdated algorithms, keeping your network resilient against emerging threats.
C. Access Control
Access control is vital for safeguarding a state wide area network. It determines who can access specific resources and data within the network. By implementing robust access control measures, organizations can prevent unauthorized users from breaching their systems.
There are various methods to enforce access controls. Role-based access control (RBAC) allows permissions based on user roles, ensuring that individuals only have the necessary privileges related to their job functions. This minimizes the risk of internal threats while streamlining user management.
Another effective strategy involves multi-factor authentication (MFA). By requiring multiple forms of verification, MFA adds an extra layer of security against potential breaches. Even if passwords are compromised, this additional step helps maintain protection.
Regular audits play a crucial role in maintaining tight access controls as well. Frequent reviews ensure that permissions remain up-to-date and aligned with current organizational needs, reducing vulnerabilities and enhancing overall security posture.
D. Network Monitoring
Network monitoring is a crucial aspect of maintaining a secure state wide area network. It involves the continuous observation of network activities to identify and address potential issues before they escalate.
With real-time data collection, administrators can track performance metrics and detect anomalies in traffic patterns. This proactive approach helps in early identification of security threats or system failures.
Tools for network monitoring range from simple software applications to complex systems that integrate with existing infrastructure. These tools provide insights into bandwidth usage, device status, and overall health of the network.
Regular audits through effective monitoring also ensure compliance with regulatory standards. By establishing clear visibility across all devices connected to the SWAN, organizations can better protect sensitive information and enhance operational efficiency.
Investing in comprehensive monitoring solutions not only optimizes performance but strengthens overall security measures as well.